What are cyber-attacks about?
Welcome back to the SEB Tech blog. This time I want to describe different types of cyber-attacks and what they mean.



Have you ever been blocked from a website that you know is safe? You're not alone.
The statement that the internet is a dangerous place will not surprise anyone. Yet, for the modern corporation, the internet has become the new corporate network – with employees using it to access data in cloud applications as well as other resources on the web. SEB is no exception.
The internet is an important part of the workplace at SEB, enabling employees to access information, email, cloud services, and various other web resources. That means employees will visit a large number of websites as they seek to do their job as efficiently as possible. It also means that it is unavoidable that they sometimes will end up on suspicious websites.
When a user clicks on a link on such a website, a malicious payload may be downloaded and executed by the browser even if the URL itself is not suspicious.
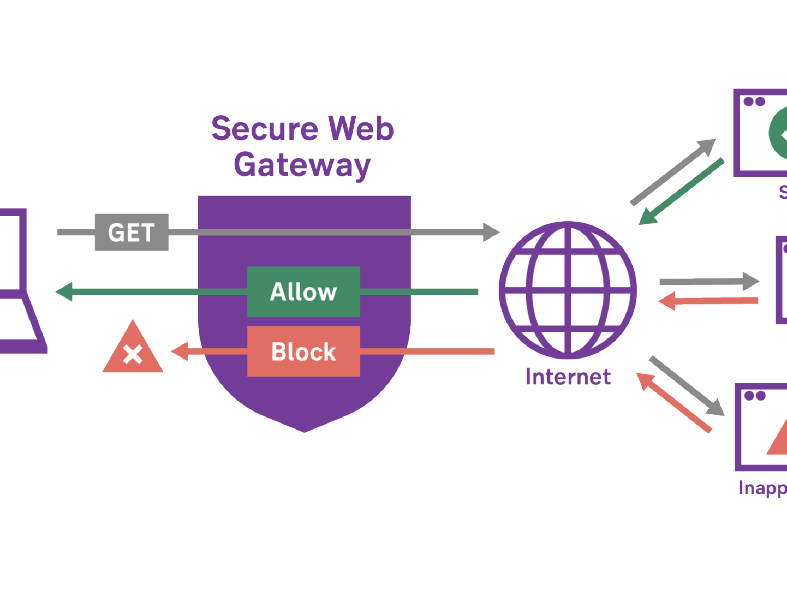
We either can block access to various websites at the expense of business productivity or incur risk by enabling wider access. For this reason, the Secure Web Gateways (SWG) are used on corporate networks to check web traffic and make sure that only safe sites are available for users while dangerous ones are blocked.
We always strive to achieve a balance between security and employee productivity. It is a difficult task that requires continuous attention and effort, as cyber-attackers constantly change their tactics in order to evade detection.
Hundreds of thousands of new sites are created every day. Many are safe and legitimate, but some are created purely for launching cyber-attacks.
To be able to handle such a number of websites in the most efficient way, Secure Web Gateways uses a URL categorization feature to check and filter website URL addresses against a database of known and categorized websites. The database has a vast number (billions) of URLs classified into different categories, such as, social networking, gambling, cloud storage, and shopping, etc.
One of those categories is called Uncategorized, and it is the primary reason for web security over-blocking, and the policy which is set to restrict access to such websites.
While real-time AI categorization can classify a majority of new websites, some sites fail to be conclusively classified into a specific category. This issue might be due to a lack of information coming from the website itself.
The number of uncategorized websites is relatively small worldwide when compared to the total number of websites. However, in the traffic on any given day they still pose a problem for many security administrators.
Before the emergence of risk level ratings and browser isolation technologies, there were virtually only two ways to handle uncategorized sites: to allow the sites or to block them. Organisations that wanted tighter security typically blocked access to uncategorized sites, which typically resulted in a greater number of help-desk calls from users wanting to gain access to blocked sites. On the other hand, if access to uncategorized sites was allowed, it typically resulted in a higher rate of malware infection and a greater number of compromised systems.
Therefore, neither option worked well, and security professionals needed a better solution. That's why Secure Web Gateway vendors started introducing browser isolation features to help with the problems caused by uncategorized sites and other risky URLs.
Browser Isolation is a cybersecurity model that aims to physically isolate an internet user's browsing activity – and the associated cyber risks – away from their local device and infrastructure.
By using Browser Isolation technology at SEB, we aim to reduce over-blocking for users by widening access to currently blocked websites and allowing access to uncategorized and potentially risky traffic while at the same time maintaining a desired security level and minimizing risks of malware infections.
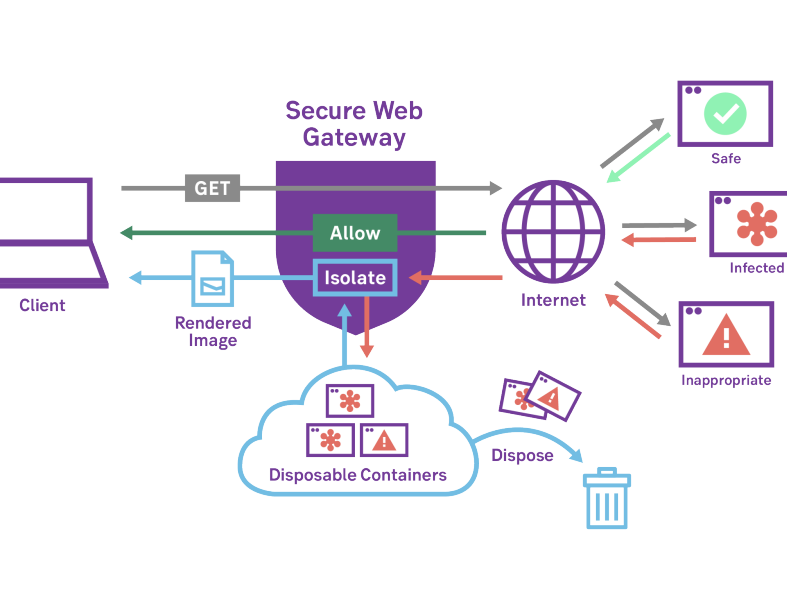
Browser Isolation executes web sessions away from endpoints on the cloud-hosted disposable containers, sending only information that has been rendered safe to users' browsers. This prevents malware from reaching the network and devices.
These disposable containers perform actual browsing actions and transmit rendered information of the remote browser window back to the users' web browser.
In this way, any malicious code — whether it is downloaded automatically or by a user's deliberate action — is kept separate from the user's device. After a session, these containers are simply deleted, with all web content and any malware inside.
We certainly think so. Just like all other cyber security teams, we want to keep our organisation from being included in any cyber-breach statistics.
We aim to achieve this by combining the Secure Web Gateway and Browser Isolation technologies. This allows us to protect users in real time from web threats targeting them from uncategorized sites or potentially unsafe URLs, while at the same time minimizing the number of support tickets requesting access to blocked sites that employees need to do their job. This helps us improve business productivity by reducing website over-blocking.
Welcome back to the SEB Tech blog. This time I want to describe different types of cyber-attacks and what they mean.

Even with a strict password policy, it becomes difficult to guarantee that passwords are strong. The most common passwords we have are cracked in a few seconds.

I think some still remember when non-functional requirements (NFR) were activities in a project plan and thus could be prioritized accordingly. However, this meant that important requirements for a system or application did not always get the focus that was needed - the time did not exist.
Do you have feedback or thoughts about future blog articles? Get in contact with us at the e-mail address below.